Security of Global Navigation Satellite Systems
The Problem
Today, it is possible to spoof a GPS receiver to any arbitrary location. Check out the video we created to demonstrate how trivial it is to spoof GPS signals today! The increasing availability of low-cost radio hardware platforms make it feasible to execute such attacks with less than few hundred dollars worth of hardware equipment.
Selected Projects
GNSS-WASP: GNSS Wide Area SPoofing
In this paper, we propose GNSS-WASP, a novel wide-area spoofing attack carried by a constellation of strategically located synchronized transmitters. Unlike known attacks, which are constrained by the attacker’s ability to track victim receivers, GNSS-WASP manipulates the positions measured by all the receivers in a target area without knowing the victim’s positions. This allows GNSS-WASP to spoof a swarm of victims to another location while preserving their true formation (i.e., their relative distances). This opens the possibility of advanced attacks that divert entire fleets of vehicles and drones in a large area without the need to track specific victims. As such, GNSS-WASP bypasses state-of-the-art spoofing countermeasures that rely on constellations of receivers with known distances and those that rely on sudden, unpredictable movements for spoofing detection. While previous works discuss the stringent requirements for perfect spoofing of multiple receivers at known fixed locations, GNSS-WASP demonstrates how to spoof any number of moving receivers at unknown positions in a large area with an error that can remain hidden behind the legitimate noise. In addition to extensive simulations, we implement a prototype of GNSS-WASP with off-the shelf software-defined radios and evaluate it on real GNSS receivers. Despite the error introduced by the proposed attack, GNSS-WASP can successfully spoof two receivers while maintaining their relative distance with an average error of 0.97 m for locations 1000 m away from the reference position. Finally, we also highlight possible countermeasures.
Related publication:
Tibaldo Christopher, Harshad Sathaye, Giovanni Camurati, Srdjan Capkun
GNSS-WASP: GNSS Wide Area SPoofing [PDF]
In USENIX Security Symposium (USENIX ’24), 2024
SPREE: A Spoofing Resistant GPS Receiver
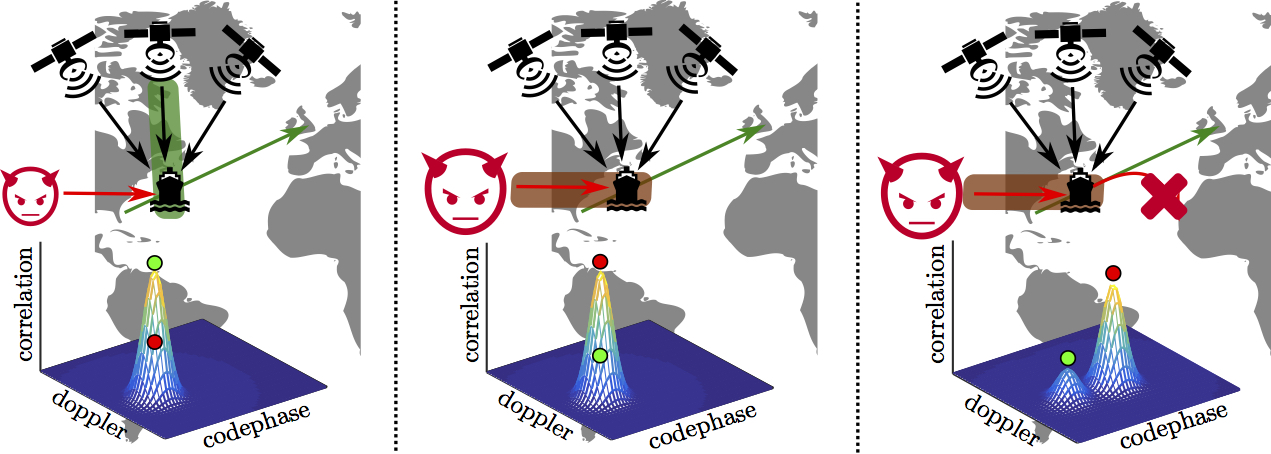
Global Positioning System (GPS) is used ubiquitously in a wide variety of applications ranging from navigation and tracking to modern smart grids and communication networks. However, it has been demonstrated that modern GPS receivers are vulnerable to signal spoofing attacks. For example, today it is possible to change the course of a ship or force a drone to land in a hostile area by simply spoofing GPS signals. Several countermeasures have been proposed in the past to detect GPS spoofing attacks. These countermeasures offer protection only against naive attackers. They are incapable of detecting strong attackers such as those capable of seamlessly taking over a GPS receiver, which is currently receiving legitimate satellite signals, and spoofing them to an arbitrary location. Also, there is no hardware platform that can be used to compare and evaluate the effectiveness of existing countermeasures in real-world scenarios.
In this work, we present SPREE, which is, to the best of our knowledge, the first GPS receiver capable of detecting all spoofing attacks described in the literature. Our novel spoofing detection technique called auxiliary peak tracking enables detection of even a strong attacker capable of executing the seamless takeover attack. We implement and evaluate our receiver against three different sets of GPS signal traces: (i) a public repository of spoofing traces, (ii) signals collected through our own wardriving effort and (iii) using commercial GPS signal generators. Our evaluations show that SPREE constraints even a strong attacker (capable of seamless takeover attack) from spoofing the receiver to a location not more than 1 km away from its true location. This is a significant improvement over modern GPS receivers that can be spoofed to any arbitrary location. Finally, we release our implementation and datasets to the community for further research and development.
Project website: https://www.spree-gnss.ch
Related publication:
Aanjhan Ranganathan, Hildur Ólafsdóttir, Srdjan Capkun
SPREE: Spoofing Resistant GPS Receiver [Paper][Bibtex]
In Proceedings of the 22nd Annual International Conference on Mobile Computing and Networking (MobiCom 2016)
On the Requirements for GPS Signal Spoofing Attacks
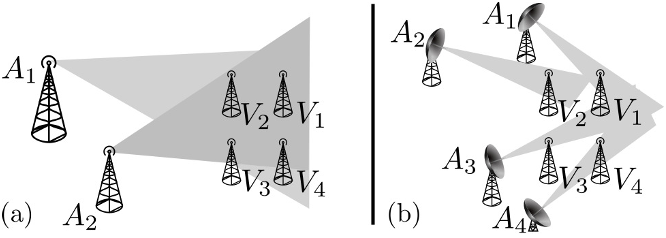
In this paper, we investigate the requirements for successful GPS spoofing attacks on individuals and groups of victims with civilian or military GPS receivers. In particular, we are interested in identifying from which locations and with which precision the attacker needs to generate its signals in order to successfully spoof the receivers.
We will show, for example, that any number of receivers can easily be spoofed to one arbitrary location; however, the attacker is restricted to only few transmission locations when spoofing a group of receivers while preserving their constellation. In addition, we investigate the practical aspects of a satellite-lock takeover, in which a victim receives spoofed signals after first being locked on to legitimate GPS signals. Using a civilian GPS signal generator, we perform a set of experiments and find the minimal precision of the attacker’s spoofing signals required for covert satellite-lock takeover.
Related publication:
Nils Ole Tippenhauer, Christina Pöpper, Kasper Bonne Rasmussen, Srdjan Capkun
On the Requirements for Successful GPS Spoofing Attacks
ACM Conference on Computer and Communications Security (CCS), 2011
Other Publications
Yu, Der-Yeuan, Aanjhan Ranganathan, Thomas Locher, Srdjan Capkun, and David Basin
Short paper: Detection of GPS spoofing attacks in power grids
In Proceedings of the 2014 ACM conference on Security and privacy in wireless & mobile networks (WiSec).