Secure Proximity Verification (Ranging)
Today, we live in a physical world in which a wide variety of applications depend on location and proximity information. The above story illustrates this through a mix of existing and future applications. Contactless access tokens (e.g., contactless smart/proximity cards, key fobs) are prevalent today in a number of systems including public transport ticketing, parking and highway toll fee collection, payment systems, electronic passports, physical access control and personnel tracking. In a typical access control application, an authorized person simply taps his smart card against a card reader setup at the entrance to gain access to an infrastructure. Smart card-based physical access control and authentication are deployed even in safety- and security-critical infrastructures such as nuclear power plants and defense research organizations. Similarly, in an electronic payment scenario, the consumer places the contactless card in close proximity (a few centimeters) to the payment terminal for making secure payments. Furthermore, modern automobiles use passive keyless entry systems (PKES) to unlock, lock or start the vehicle when the key fob is in close proximity without any user interaction. PKES also enhances security in scenarios e.g., where the user forgets to manually lock the car or in the case of a jamming attack.
In this project, we demonstrate that existing systems are insecure and show various possible attacks. Furthermore, we design and implement several countermeasures that prevents an attacker from modifying the distance measurements (proximity) thereby enhancing the security of these systems.
UWB-Based Relay Protection for Secure Contactless Payments
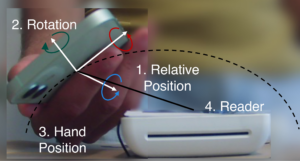
Contactless payments are now widely used and are expected to reach $10 trillion worth of transactions by 2027. Although convenient, contactless payments are vulnerable to relay attacks that enable attackers to execute fraudulent payments. A number of countermeasures have been proposed to address this issue, including Mastercard’s relay protection mechanism. These countermeasures, although effective against some Commercial off-the-shelf (COTS) relays, fail to prevent physical layer relay attacks. In this work, we leverage the Ultra-Wide Band (UWB) radios incorporated in major smartphones, smartwatches, tags and accessories, and introduce PURE, the first UWB-based relay protection that integrates smoothly into existing contactless payment standards, and prevents even the most sophisticated physical layer attacks. PURE extends EMV payment protocols that are executed between cards and terminals, and does not require any modification to the backend of the issuer, acquirer, or payment network. PURE further tailors UWB ranging to the payment environment (i.e., wireless channels) to achieve both reliability and resistance to all known physical layer distance reduction attacks against UWB 802.15.4z. We implement PURE within the EMV standard on modern smartphones, and evaluate its performance in a realistic deployment. Our experiments show that PURE provides a sub-meter relay protection with minimal execution overhead (41 ms). We formally verify the security of PURE’s integration within Mastercard’s EMV protocol using the Tamarin prover.
Related Publication:
Coppola Daniele, Camurati Giovanni, Anliker Claudio, Hofmeier Xenia, Schaller Patrick, Basin David, Capkun Srdjan
PURE: Payments with UWB RElay-protection
in USENIX Security Symposium (USENIX ’24), 2024 [PDF]
How Clocks Break UWB Secure Ranging
Due to its suitability for wireless ranging, Ultra-Wide Band (UWB) has gained traction over the past years. UWB chips have been integrated into consumer electronics and considered for security-relevant use cases, such as access control or contactless payments. However, several publications in the recent past have shown that it is difficult to protect the integrity of distance measurements on the physical layer. In this paper, we identify transceiver clock imperfections as a new, important parameter that has been widely ignored so far. We present Mix-Down and Stretch-and-Advance, two novel attacks against the current (IEEE 802.15.4z) and the upcoming (IEEE 802.15.4ab) UWB standard, respectively. We demonstrate Mix-Down on commercial chips and achieve distance reductions from 10 m to 0 m. For the Stretch-and-Advance attack, we show analytically that the current proposal of IEEE 802.15.4ab allows reductions of over 90 m. To prevent the attack, we propose and analyze an effective countermeasure.
Related Publication:
Anliker Claudio, Camurati Giovanni, Capkun Srdjan
Time for Change: How Clocks Break UWB Secure Ranging
in USENIX Security Symposium (USENIX ’23), 2023 [PDF]
Ghost Peak: Practical Distance Reduction Attacks Against HRP UWB Ranging
We present the first over-the-air attack on IEEE 802.15.4z High-Rate Pulse Repetition Frequency (HRP) Ultra-Wide Band (UWB) distance measurement systems. Specifically, we demonstrate a practical distance reduction attack against pairs of Apple U1 chips (embedded in iPhones and AirTags), as well as against U1 chips inter-operating with NXP and Qorvo UWB chips. These chips have been deployed in a wide range of phones and cars to secure car entry and start and are projected for secure contactless payments, home locks, and contact tracing systems. Our attack operates without any knowledge of cryptographic material, results in distance reductions from 12m (actual distance) to 0m (spoofed distance) with attack success probabilities of up to 4%, and requires only an inexpensive (USD 65) off-the-shelf device. Access control can only tolerate sub-second latencies to not inconvenience the user, leaving little margin to perform time-consuming verifications. These distance reductions bring into question the use of UWB HRP in security-critical applications.
Related Publication:
Patrick Leu, Giovanni Camurati, Alexander Heinrich, Marc Roeschlin, Claudio Anliker, Matthias Hollick, Srdjan Capkun, Jiska Classen
Ghost Peak: Practical Distance Reduction Attacks Against HRP UWB Ranging
in USENIX Security Symposium (USENIX ’22), 2022 [PDF]
Fundamental Primitive for Secure Distance Measurement
Secure distance measurement and therefore secure Time-of-Arrival (ToA) measurement is critical for applications such as contactless payments, passive-keyless entry and start systems, and navigation systems. This paper initiates the study of Message Time of Arrival Codes (MTACs) and their security. MTACs represent a core primitive in the construction of systems for secure ToA measurement. By surfacing MTACs in this way, we are able for the first time to formally define the security requirements of physical-layer measures that protect ToA measurement systems against attacks. Our viewpoint also enables us to provide a unified presentation of existing MTACs (such as those proposed in distance-bounding protocols and in a secure distance measurement standard) and to propose basic principles for protecting ToA measurement systems against attacks that remain unaddressed by existing mechanisms. We also use our perspective to systematically explore the tradeoffs between security and performance that apply to all signal modulation techniques enabling ToA measurements.
Related Publication:
Patrick Leu, Mridula Singh, Marc Roeschlin, Kenneth G. Paterson and Srdjan Capkun
Message Time of Arrival Codes: A Fundamental Primitive for Secure Distance Measurement
in IEEE Symposium on Security and Privacy (S&P), 2020 (to appear) [PDF]
Modulation technique to detect distance enlargement attack 
Mobile autonomous systems, robots, and cyber-physical systems rely on accurate positioning information. To conduct distance-measurement, two devices exchange signals and, knowing these signals propagate at the speed of light, the time of arrival is used for distance estimations. Existing distance-measurement techniques are incapable of protecting against adversarial distance enlargement — a highly devastating tactic in which the adversary reissues a delayed version of the signals transmitted between devices, after distorting the authentic signal to prevent the receiver from identifying it. The adversary need not break crypto, nor compromise any upper- layer security protocols for mounting this attack. No known solution currently exists to protect against distance enlargement. We present Ultra-Wideband Enlargement Detection (UWB-ED), a new modulation technique to detect distance enlargement attacks, and securely verify distances between two mutually trusted devices. We analyze UWB-ED under an adversary that injects signals to block/modify authentic signals. We show how UWB-ED is a good candidate for 802.15.4z Low Rate Pulse and the 5G standard.
Related Publication:
Mridula Singh, Patrick Leu, AbdelRahman Abdou, Srdjan Capkun
UWB-ED: Distance Enlargement Attack Detection in Ultra-Wideband
In Proceedings of the USENIX Security Symposium, 2019 [PDF]
UWB-PR modulation to secure distance measurement
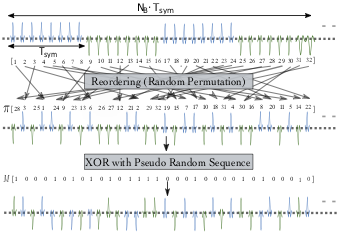
Physical layer attacks allow attackers to manipulate (spoof) ranging and positioning. These attacks had real world impact and allowed car thefts, executions of unauthorised payments and manipulation of navigation. UWB impulse radio (UWB-IR) has emerged as a prominent technique for precise ranging that allows high operating distances despite power constraints by transmitting multi-pulse symbols. Unfortunately, longer symbols make UWB-IR vulnerable to physical layer attacks. Currently, none of the existing systems is precise, performant and secure at same time. We present UWB with Pulse Reordering (UWB-PR), the first modulation scheme that secures distance measurement between two mutually trusted devices against all physical-layer attacks without sacrificing performance and irrespective of the environment or attacker. We analyze the security of UWB-PR under the attacker that fully controls the communication channel and show that UWB-PR resists even such a strong attacker. We evaluate UWB-PR within an UWB system building on IEEE~802.15.4f and show that it achieves distances of up to 93m with 10cm precision (LoS).
Related Publication:
Mridula Singh, Patrick Leu, Srdjan Capkun
UWB with Pulse Reordering: Securing Ranging against Relay and Physical Layer Attacks
In Proceedings of the Network and Distributed System Security Symposium (NDSS), 2019 [PDF]
Attacks On the Security of Carrier Phase-based Ranging
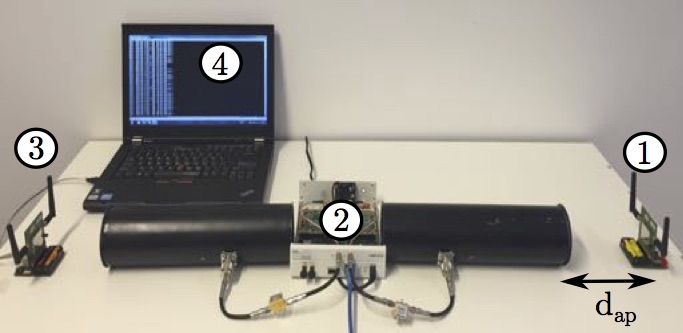
Multicarrier phase-based ranging is fast emerging as a cost-optimized solution for a wide variety of proximity-based applications due to its low power requirement, low hardware complexity and compatibility with existing standards such as ZigBee and 6LoWPAN. Given potentially critical nature of the applications in which phase-based ranging can be deployed (e.g., access control, asset tracking), it is important to evaluate its security guarantees. Therefore, in this work, we investigate the security of multicarrier phase-based ranging systems and specifically focus on distance decreasing relay attacks that have proven detrimental to the security of proximity-based access control systems (e.g., vehicular passive keyless entry and start systems). We show that phase-based ranging, as well as its implementations, are vulnerable to a variety of distance reduction attacks. We describe different attack realizations and verify their feasibility by simulations and experiments on a commercial ranging system. Specifically, we successfully reduced the estimated range to less than 3 m even though the devices were more than 50 m apart. We discuss possible countermeasures against such attacks and illustrate their limitations, therefore demonstrating that phase-based ranging cannot be fully secured against distance decreasing attacks.
Related Publication:
Hildur Olafsdottir, Aanjhan Ranganathan, Srdjan Capkun
On the Security of Carrier Phase-based Ranging
Arxiv e-print (arXiv:1610.06077) [PDF]
Physical-layer Attacks on Chirp-based Ranging Systems
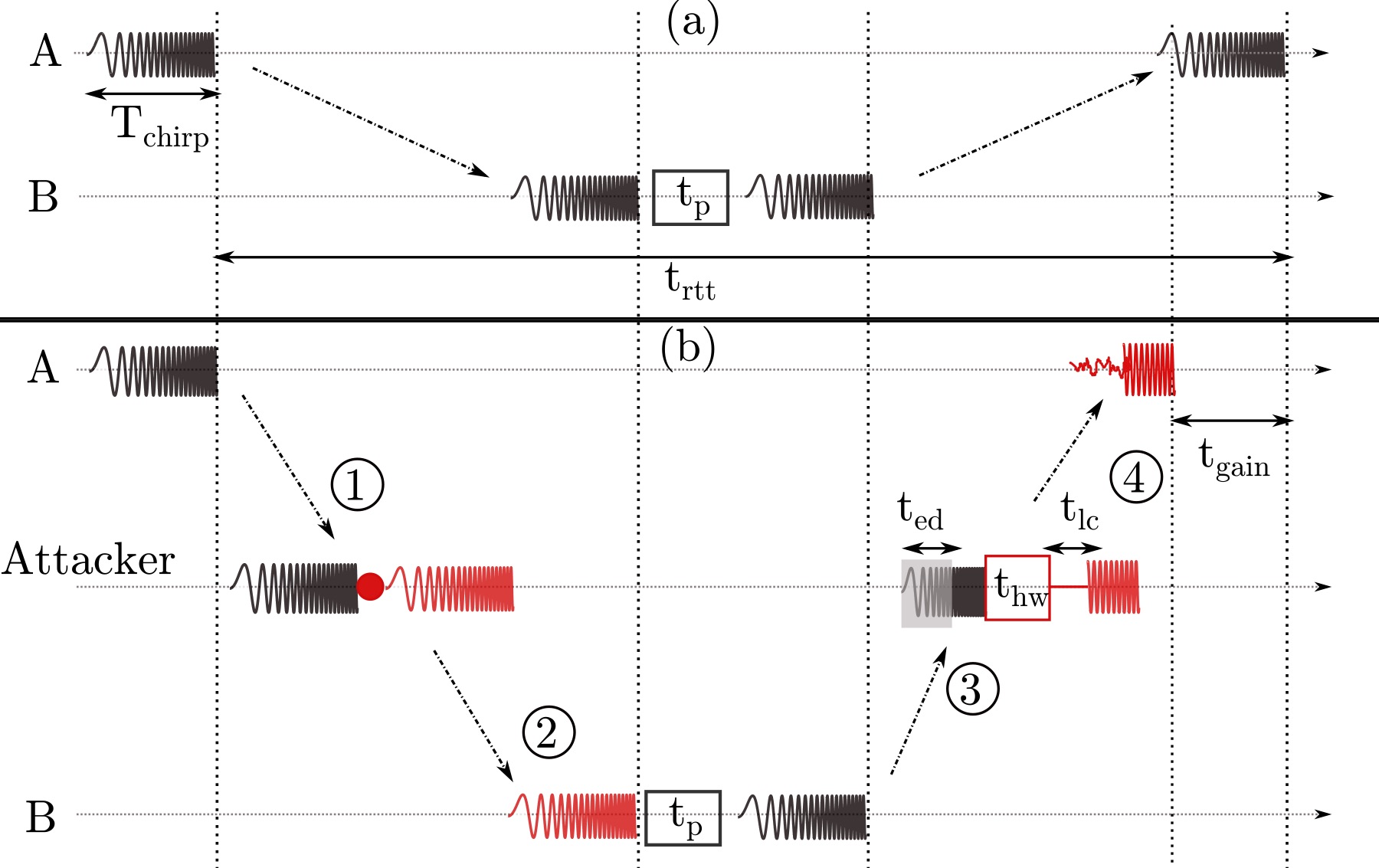
Chirp signals have been extensively used in radar and sonar systems to determine distance, velocity and angular position of objects and in wireless communications as a spread spectrum technique to provide robustness and high processing again. Recently, several standards have adopted chirp spread spectrum (CSS) as an underlying physical-layer scheme for precise, low-power and low-complexity real-time localization. While CSS-based ranging and localization solutions have been implemented and deployed, their security has so far not been analyzed. In this work, we analyze CSS-based ranging and localization systems. We focus on distance decreasing relay attacks that have proven detrimental for the security of proximity-based access control systems (e.g., passive vehicle keyless entry and start systems). We describe a set of distance decreasing attacks realizations and verify their feasibility by simulations and experiments on a commercial ranging system. Our results demonstrate that an attacker is able to effectively reduce the distance measured by chirp-based ranging systems from 150 m to 700 m depending on chirp configuration. Finally, we discuss possible countermeasures against these attacks.
Related Publication:
Aanjhan Ranganathan, Boris Danev, Aurélien Francillon, Srdjan Capkun
Physical-Layer Attacks on Chirp-based Ranging Systems
In Proceedings of ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2012
Relay Attacks on Passive Keyless Entry Systems in Modern Cars
We demonstrate relay attacks on Passive Keyless Entry and Start (PKES) systems used in modern cars. We build two efficient and inexpensive attack realizations, wired and wireless physical-layer relays, that allow the attacker to enter and start a car by relaying messages between the car and the smart key. Our relays are completely independent of the modulation, protocol, or presence of strong authentication and encryption. We perform an extensive evaluation on 10 car models from 8 manufacturers. Our results show that relaying the signal in one direction only (from the car to the key) is sufficient to perform the attack while the true distance between the key and car remains large (tested up to 50 meters, non line-of-sight). We also show that, with our setup, the smart key can be excited from up to 8 meters. This removes the need for the attacker to get close to the key in order to establish the relay. We further analyze and discuss critical system characteristics. Given the generality of the relay attack and the number of evaluated systems, it is likely that all PKES systems based on similar designs are also vulnerable to the same attack. Finally, we propose immediate mitigation measures that minimize the risk of relay attacks as well as recent solutions that may prevent relay attacks while preserving the convenience of use, for which PKES systems were initially introduced.
Related Publication:
Aurelien Francillon, Boris Danev, Srdjan Capkun
Relay Attacks on Passive Keyless Entry and Start Systems in Modern Cars
In Proceedings of the Network and Distributed System Security Symposium (NDSS), 2011
Preceding technical report: Cryptology ePrint Archive: Report 2010/332, 2010 [PDF]
Countermeasures
Distance modification attacks have serious implications (some examples illustrated above): an attacker can gain entry into a restricted area, make fraudulent payments or steal a car by simply relaying the communications between the reader and the card which is several meters away without the knowledge of the card’s owner. In order to prevent such distance modification attacks, these systems must be enhanced with distance bounding. Distance bounding guarantees an upper bound on the physical distance between two devices, a verifier, and a prover. Below are some of the solutions we developed to protect proximity-based access control and authentication systems against distance modification attacks.
Related Publications:
Aanjhan Ranganathan, Srdjan Capkun
Are We Really Close? Verifying Proximity in Wireless Systems
in IEEE Security & Privacy Magazine, 2016 [PDF]
Aanjhan Ranganathan, Boris Danev and Srdjan Capkun
Proximity Verification for Contactless Access Control and Authentication Systems
31st Annual Computer Security Applications Conference (ACSAC), 2015 [PDF (PDF, 5.1 MB)]
Nils Ole Tippenhauer, Heinrich Luecken, Marc Kuhn and Srdjan Capkun
UWB Rapid-Bit-Exchange System for Distance Bounding
In Proceedings of the ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2015
Aanjhan Ranganathan, Nils Ole Tippenhauer, Boris Skoric, Dave Singelee and Srdjan Capkun
Design and Implementation of a Terrorist-Fraud Resilient Distance Bounding System
In Proceedings of 17th European Symposium on Research in Computer Security (ESORICS), 2012
Srdjan Capkun, Karim El Defrawy, Gene Tsudik
Group Distance Bounding Protocols (short paper)
In Proceedings of the 4th International Conference on Trust and Trustworthy Computing (TRUST), 2011
Kasper Bonne Rasmussen, Srdjan Capkun
Realization of RF Distance Bounding
In Proceedings of the USENIX Security Symposium, 2010 [PDF (PDF, 946 KB) | bibtex (BIB, 228 Bytes)]
Marc Kuhn, Heinrich Luecken, Nils Ole Tippenhauer,
UWB Impulse Radio Based Distance Bounding
In Proceedings of WPNC (Workshop on Positioning, Navigation and Communication), 2010 [PDF (PDF, 5 KB) | bibtex (BIB, 5 KB)]
Nils Ole Tippenhauer, Kasper Bonne Rasmussen, Srdjan Capkun
Secure Ranging With Message Temporal Integrity
Cryptology ePrint Archive: Report 2009/602, 2009 [PDF (PDF, 526 KB) | bibtex (BIB, 255 Bytes)]
Kasper Bonne Rasmussen, Claude Castelluccia, Thomas S. Heydt-Benjamin, Srdjan Capkun
Proximity-based Access Control for Implantable Medical Devices
In Proceedings of the ACM Conference on Computer and Communications Security (CCS), 2009 [PDF (PDF, 470 KB) | bibtex (BIB, 399 Bytes)]
Nils Ole Tippenhauer, Srdjan Capkun
ID-based Secure Distance Bounding and Localization
In Proceedings of ESORICS (European Symposium on Research in Computer Security), 2009 [PDF (PDF, 559 KB) | bibtex (BIB, 5 KB)]