Ghost Peak: Practical Distance Reduction Attacks Against HRP UWB Ranging
Patrick Leu1*, Giovanni Camurati1*, Alexander Heinrich2, Marc Roeschlin1, Claudio Anliker1, Matthias Hollick2, Srdjan Capkun1, and Jiska Classen2
1ETH Zurich and 2TU Darmstadt *Contributed equally

Ghost Peak in a nutshell
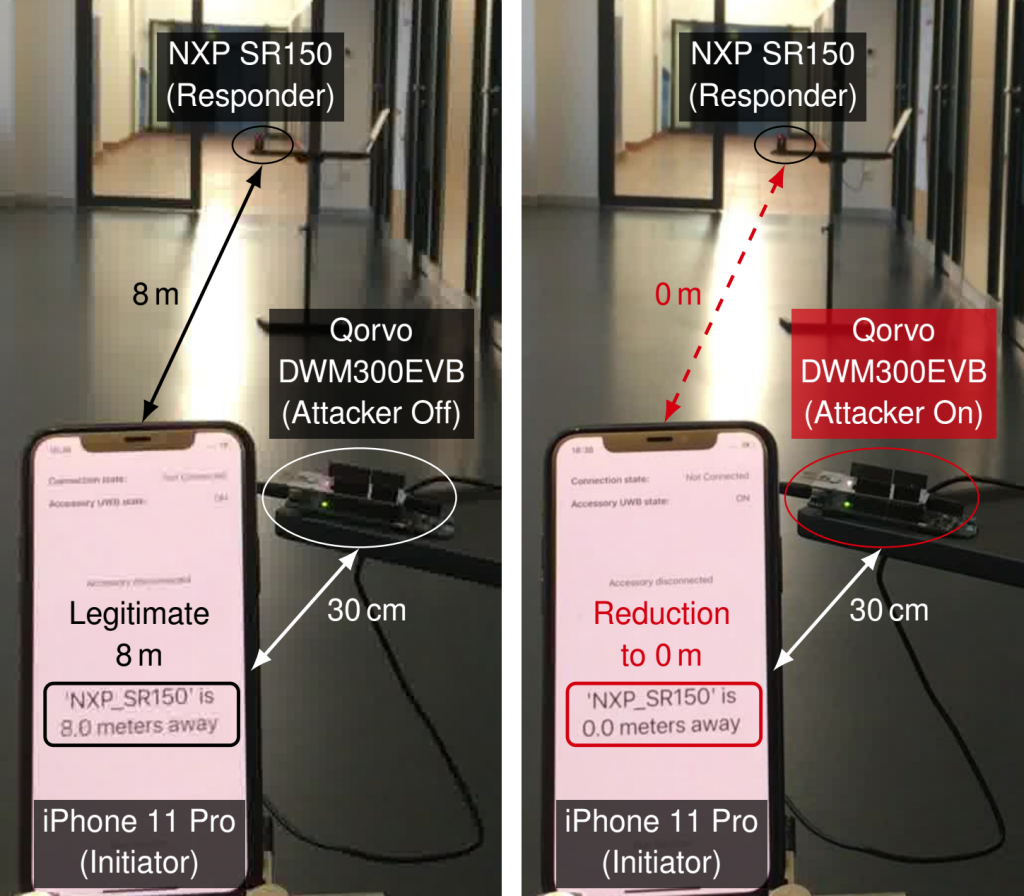
Ghost Peak is the first practical distance-reduction attack on IEEE 802.15.4z High-Rate Pulse Repetition (HRP) Ultra-Wide-Band (UWB). With Ghost Peak, an over-the-air attacker can reduce measured distances from a pair of Apple U1 chips (deployed in iPhones, AirTags, and HomePods) by several meters (e.g., 12m to 0m). The same is possible when a U1 chip interoperates with NXP (SR40/150) and Qorvo (DWM3000) chips. Ghost Peak does not leverage any knowledge about cryptographic material, it can be implemented with a 65 USD off-the-shelf device. Ghost Peak brings into question the use of HRP UWB for access control (e.g., car entry and start), mobile payments, and other security-critical applications.
USENIX Security 2022 Paper
USENIX Security 2022 Slides
USENIX Security 2022 Video
Code
UWB Sniffer
ESCAR 2021 Slides
CANS 2021 Keynote
Background
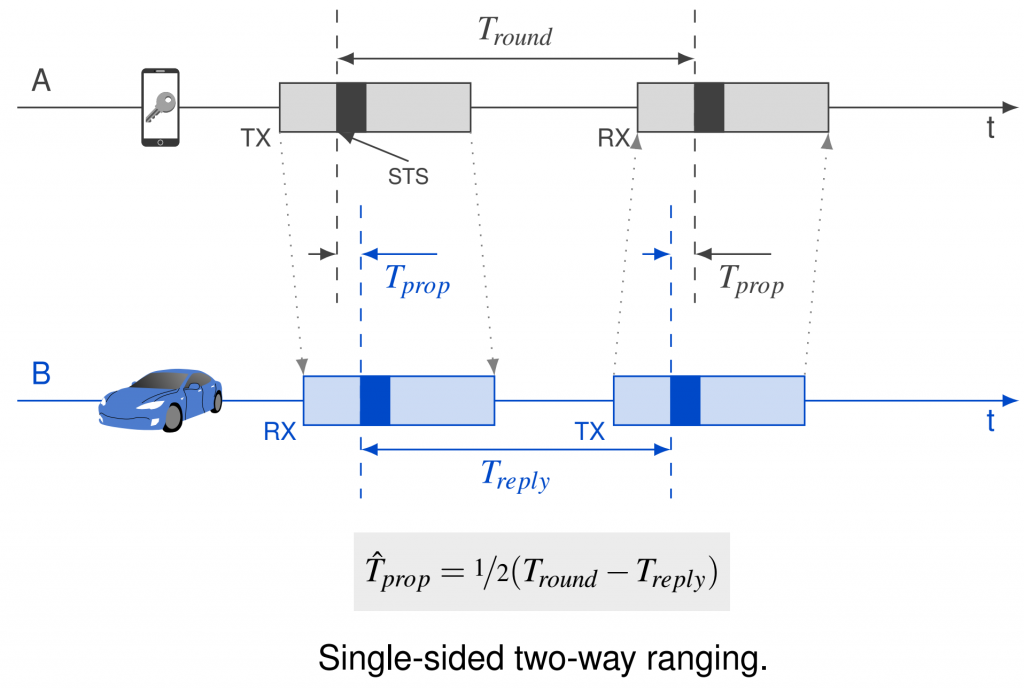
Two-way ranging
In single-sided two-way ranging, two devices measure their relative distance by estimating the time spent by a radio signal traveling at the speed of light to propagate from one device to the other and back. Two-sided two-way ranging follows the same principle but it uses three messages to compensate for clock offset errors.
To prevent distance-reduction attacks, HRP UWB packets contain an unpredictable field called Scrambled Timestamp Sequence (STS). The STS sequences are generated with AES and are cryptographically secure. Being unable to predict the STS values, the attacker cannot inject rogue messages in advance compared to the legitimate signals or replay messages that were recorded in an earlier measurement (no distance-reduction).
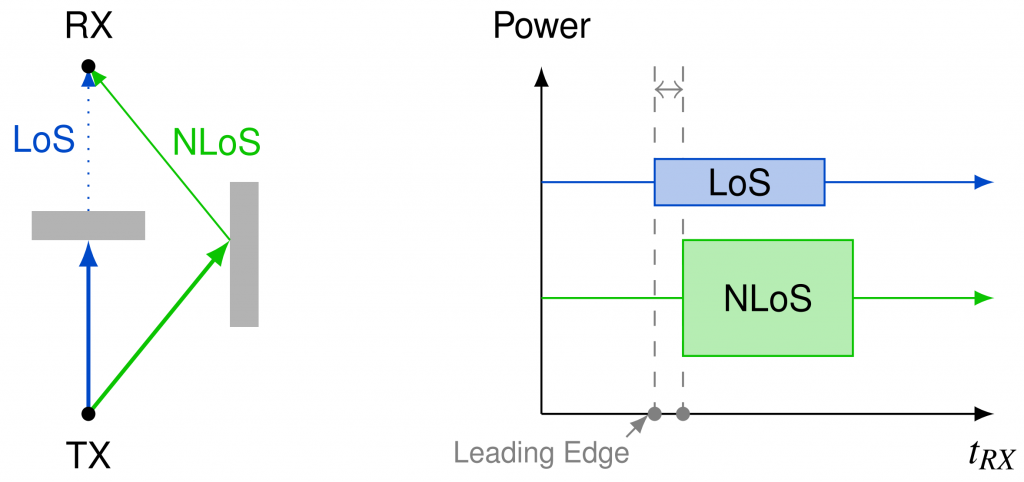
Leading-edge detection
In HRP UWB, the receiver computes the Channel Impulse Response (CIR) to detect the arrival of a packet and its precise time. In real-world conditions, multiple-copies of the transmitted signal arrive at the receiver through multiple paths, at different power. In non-line-of-sight conditions, the late copy might be even stronger than the earliest copy. For this reason, when the receiver detects a strong peak in the CIR, it also performs a back-search to look for smaller earlier peaks. Distinguishing a legitimate weak early peak from a signal injected by an attacker is not an easy problem. Previous work has shown by means of simulation that for a given receiver design there is a trade-off between performance (finding the real distance in non-line-of-sight conditions) and security (avoiding to misclassify attacker’s injected noise as an early copy of the legitimate signal).
The Attack
Threat model
Two victim devices measure their relative distance using HRP UWB two-way ranging.
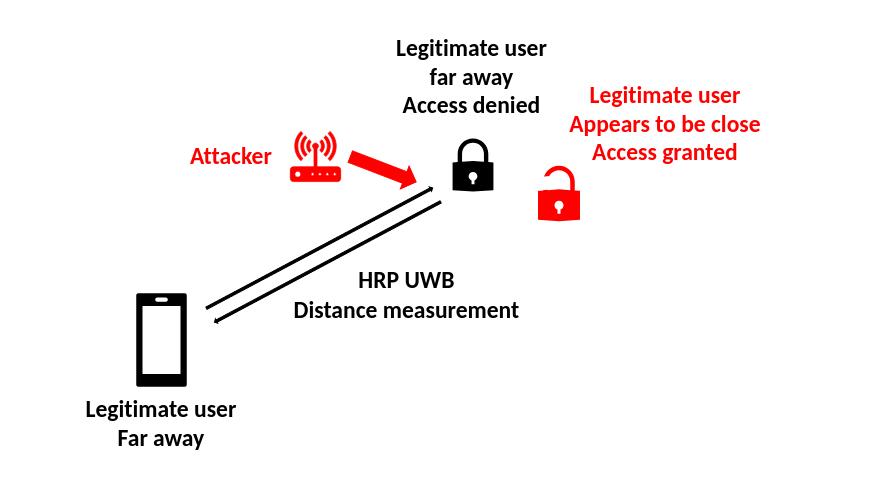
The attacker sits in range of the victims (but without need of physical access), does not leverage any knowledge about cryptographic keys or values of the STS in general, and is able to receive and transmit HRP UWB packets. By injecting a radio signal in one or both victims, the attacker tricks them into computing a wrong distance, shorter than the real one. Distance reduction tricks one of the devices into believing the other one is close, with severe consequences on applications such as access control.
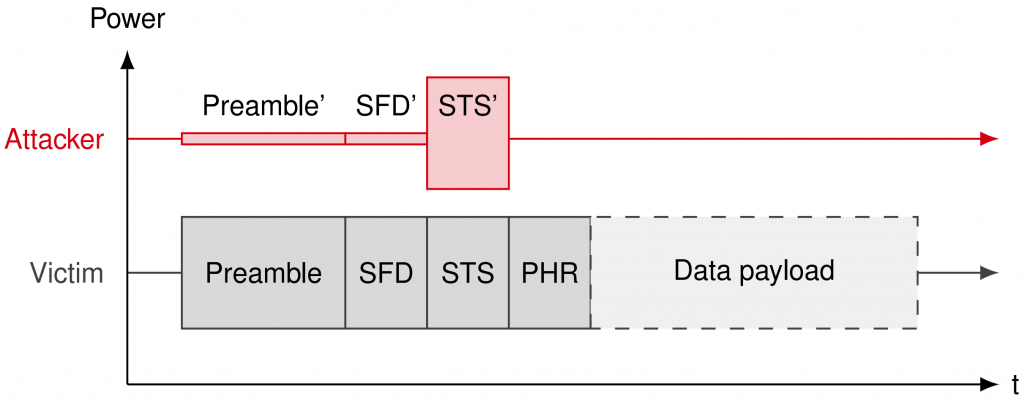
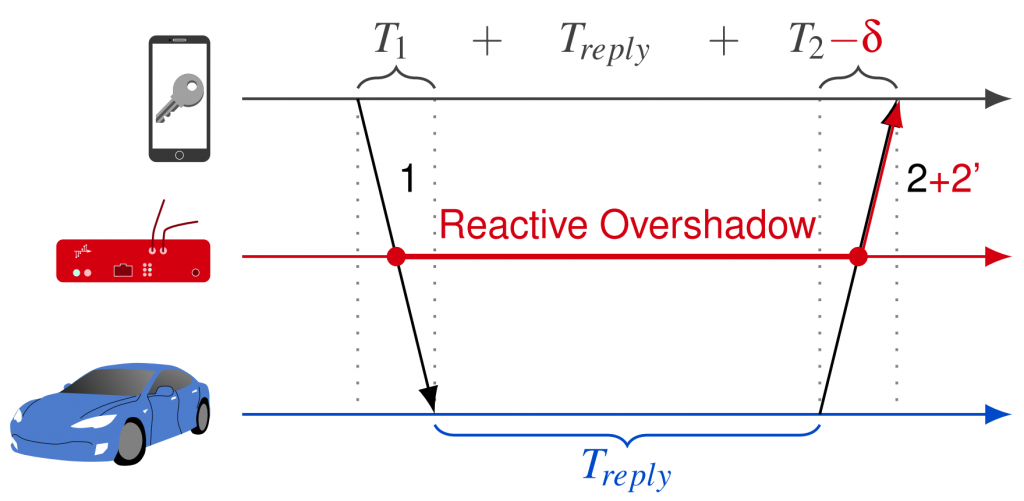
Working principle
The goal of the attack is to inject a malicious signal that tricks the leading-edge detection algorithm of the HRP UWB devices (tricking it into misclassifying a “ghost peak” as an early-copy of the legitimate signal, reducing distance). The attacker listens on the radio channel and waits for the first packet of a two-way ranging sequence. This is used as a trigger to overlay a malicious signal to one of the following packets in the sequence. The malicious signal is a packet made of preamble, frame delimiter and (random) STS. At the victim receiver, this additional signal produces a “ghost peak” that is misclassified as an early copy of the legitimate signal, causing a distance reduction. The power of individual fields and other parameters are crafted to cause distance reductions, but not jamming or other reception errors.
Attacking different sequences
In practice, ranging sequences are often made of more than one round. For example, two-sided two-way ranging computes the distance by combining two rounds to reduce errors due to clock offsets. Ghost Peak can selectively chose which packet(s) to attack with one of more attack devices. This gives the attacker the freedom to chose which side(s) of the communication to attack and has different effects on the distribution of the reductions. A detailed mathematical explanation is available in the paper.
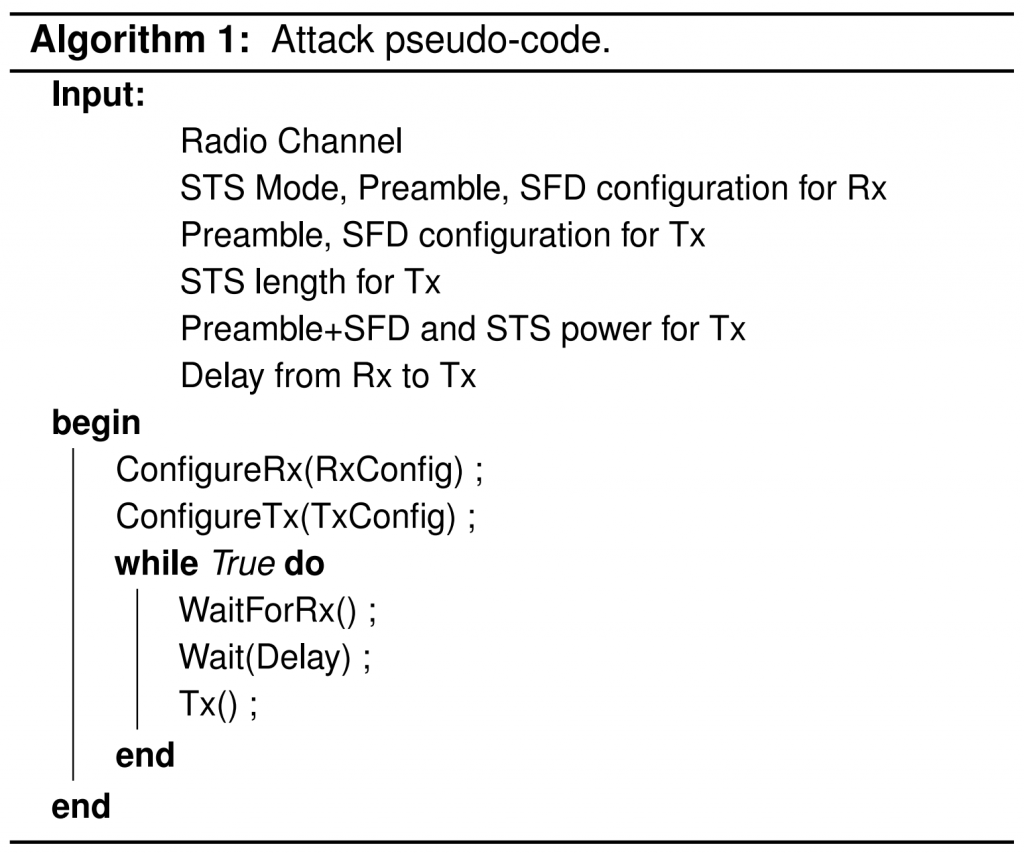
Implementation
We implemented the attack with a cheap (65 USD) off-the-shelf device (QORVO DWM3000EVB controlled by a Nordic Semiconductor nRF52DK). The same device is used to analyze the ranging sequences and their timings to configure the attacks.
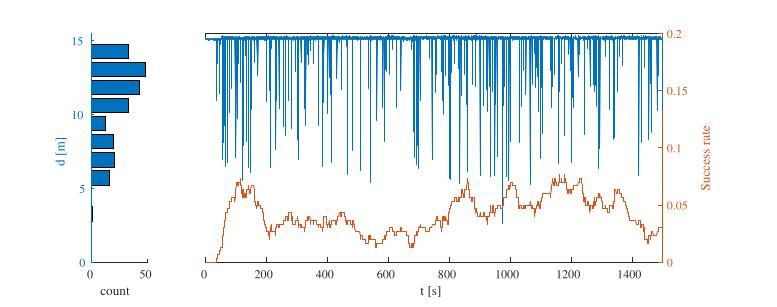
Results
We evaluated the attack in an indoor line-of-sight setting with victim devices placed at various distances. For example, a 15min trace of the attack mounted against two iPhones running NearbyInteraction and being placed at 15m relative distance reveals distance reductions of up to 12m, with an overall success rate of ca. 4%. We also evaluated different device pairings, i.e., iPhone-AirTag, iPhone-HomePod, iPhone-NXP, and iPhone-Qorvo, resulting in similar outcomes. The attack affects the Time-of-Arrival (ToA) measurement of the second or third frame of the ranging exchange. Successfully reducing the ToA of multiple frames of the ranging procedure has a cumulative effect. Attacking the second frame results in a reduction of up to ca. 10m, attacking the third frame can add up to ca. 5m. Although the attack in each pairing scenario targets the ToA measurement of the U1 chip, both entities taking part in the ranging procedure report erroneous distances (i.e., also Qorvo DWM3000 and NXP SR040/SR150).
Impact
Distance-reduction attacks are a serious threat to access control and other security-critical applications that rely on securely detecting the physical proximity of the legitimate user (e.g., car entry and start systems, mobile payments, and contact tracing).
However, HRP UWB security relies on obscure design choices at the receiver and the security level cannot be written in closed form. Ghost Peak demonstrates practical attacks with inexpensive off-the-shelf equipment. Such attacks can reduce distance from 12m to 0m with a good success rate. The short latency with which access control systems have to take decisions provides little margin to combine multiple measurements. The tradeoff between performance and security limits the guarantees that a given design can provide without increasing its complexity. Even if only one party of the ranging is vulnerable, the measurements on both sides will be accepted. Overall, these attacks question the use of HRP UWB for security applications and are a call for more analysis on the security level it can provide.
Update: Ghost Peak attacks are successful also on a pair of Qorvo DWM3000EVB devices performing SS-TWR (with STS Mode 1 and STS sequence generated with AES and secret key unknown to the attacker). Over a period of ~72h under attack performed by a third Qorvo device, we were able to cause 42 successful reductions. During a reduction, the check on the STS quality succeeds but the reported distance is several meters smaller than the real one. Reductions are also visible in double-sided two-way ranging. In conclusion, distance reduction attacks at the physical layer are possible against more than one commercial implementation of UWB HRP.
Gallery

During the attack distance is reduced and the he HomePod Music interaction panel opens on the iPhone.